Recently I was training a team in Clean Code for Embedded Systems. The team were very keen to define a coding standard, but as we talked, it became increasingly clear they were more interested in what I would call a coding style. Let me start with a couple of definitions that I use Code Style:...
Category: Software Development
All posts relating to continuous integration
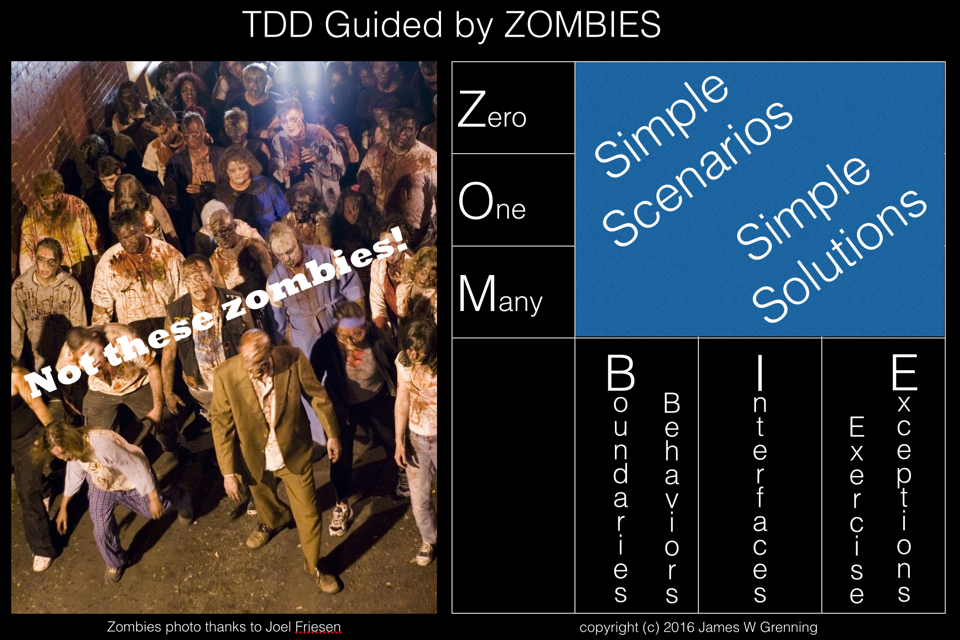
TDD Zombies
When I first used TDD I read James Grenning’s book Test Driven Development for Embedded C. In this book James proposed following a pattern for developing tests to test for zero, then one and then many (ZOM). Recently he has developed this idea further into ZOMBIE testing. Z – Zero O – One M – Many...
The Pragmatic Programmer
I think I originally read The Pragmatic Programmer by Andrew Hunt and David Thomas a good ten or fifteen years ago. I’ve just taken a couple of days while between contracts to re-read the book. I was very pleased to find that the book is just as fresh as I remember, 70 great pragmatic tips to help...
Learning Python
Python has never been a language I have had to know well. I’ve adapted existing scripts, I’ve created a few simple scripts from scratch. But I haven’t learnt it properly, just the parts I’ve needed. I decided it was about time I learnt the language properly. A friend recommended that I take a look at python koans....
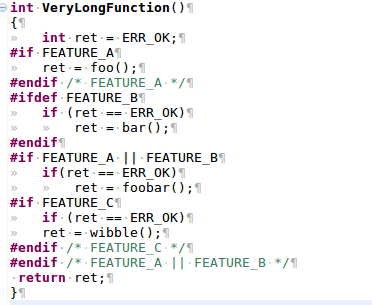
Refactoring C to Remove Feature Flags
You’ve read the books on Refactoring, on working with legacy code, on Unit Testing and on TDD. Then you look at the codebase you’ve inherited, it’s written in C, and it’s riddled with conditional compilation. Where do you start? In years gone by feature flags were widely used in embedded systems as a means of having...
Developing the CODESYS runtime with TDD
I was recently working in the CODESYS runtime again, developing some components for a client and I thought the experience wold make the basis of a good post on bringing legacy code into a test environment, to enable Test Driven Development (TDD)The CODESYS runtime is a component based system, and for most device manufacturers is...
Static analysis with Cppcheck in eclipse CDT and Jenkins
Static analysis tools look for a wide range of potential errors with code that compilers do not look for. Cppcheck is a an open source static analysis tool, it is extensible and being actively developed. These are the sorts of errors that can be found Out of bounds checking Memory leaks checking Detect possible...
gcov code coverage in eclipse and Jenkins
Introduction This post gives step by step instructions for adding code coverage with gcov to a google test eclipse project that is built as part of a CI process on Jenkins. This post starts from the point of already having a project compiled by a gnu compiler, in an eclipse CDT project that is being...
Automating eclipse CDT build on Jenkins
In my previous posts I have shown how to setup Jenkins to work with SVN and trac running on the Raspberry PI. I have also shown how to configure eclipse to work with google test and how to configure eclipse to work with SVN and trac. This post covers how to automate the build of...
Integrating SVN, trac and jenkins with eclipse CDT
I have previously posted on how to install trac, SVN and jenkins on the Raspberry Pi, and also on how to install (see the bottom of this post for related posts). When using Eclipse there are helpful plugins that tightly integrate all of these tools. This post covers the installation and configuration of these tools....